Entra ID Verified ID
Chapter 1 : An Example
Let’s delve into an illustrative scenario.
When individuals are onboarded by a company today, the HR department typically requests various forms of identification such as passports or driving licenses, along with educational and professional certificates, and experience letters. This process is crucial for confirming the legitimacy of the candidate being hired, especially considering the prevalent ease of document forgery.
However, managing this verification process can be cumbersome work for HR teams, as they often need to engage third-party vendors for external verification. This reliance on external parties adds layers of complexity and increases the workload for HR professionals.
To address this challenge, the concept of Verified ID has emerged. The Verified ID system aims to streamline the verification process and enhance its efficiency. Please refer to the diagram below for a clearer understanding:
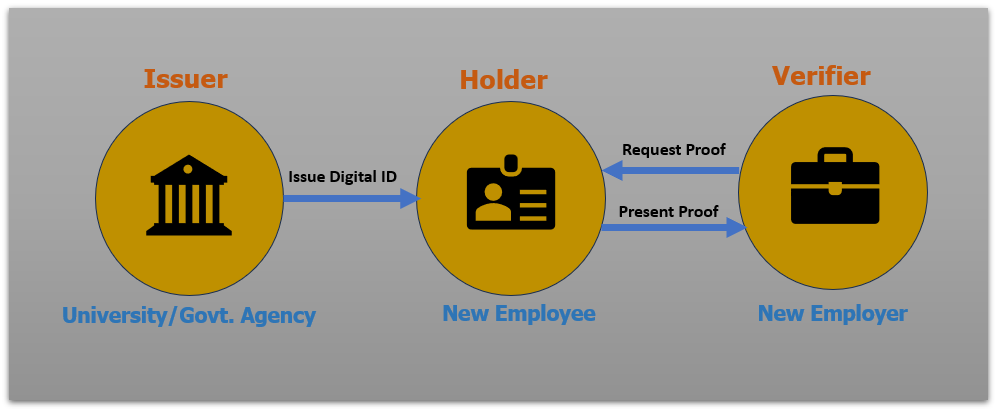
By implementing a Verified ID system, companies can automate and centralize the verification process, reducing the burden on HR teams and ensuring the authenticity of candidate credentials more effectively.
Chapter 2 : The Concept
The concept of a Verified ID operates on a straightforward principle. Initially, an Issuer, which could be an educational institution, government entity, or similar authority, issues a Digital ID or Certificate to an individual. These certificates, such as Graduation Certificates, Passports, or Driving Licenses, are digitally signed by the Issuing Authority, establishing their authenticity beyond doubt.
When the individual, now referred to as the Holder, needs to present their credentials to a Verifier, such as a prospective employer, they simply provide their Digital ID proof. Since this Digital ID is digitally signed by the Issuing Authority, the Verifier can accept it without the need for additional verification steps. This streamlines the verification process and eliminates the need for redundant checks.
In the case of Microsoft Entra ID Verified ID, the same principle applies. Microsoft Entra ID issues a Signed Digital ID to its users, allowing them to demonstrate their corporate identity confidently. This Verified ID enables Entra ID users to seamlessly prove their affiliation with their company to it’s Internal resources like Data/Devices/Apps as well as to a third-party providers, simplifying identity verification procedures across various platforms. Both the scenarios are illustrated in the below Diagram.
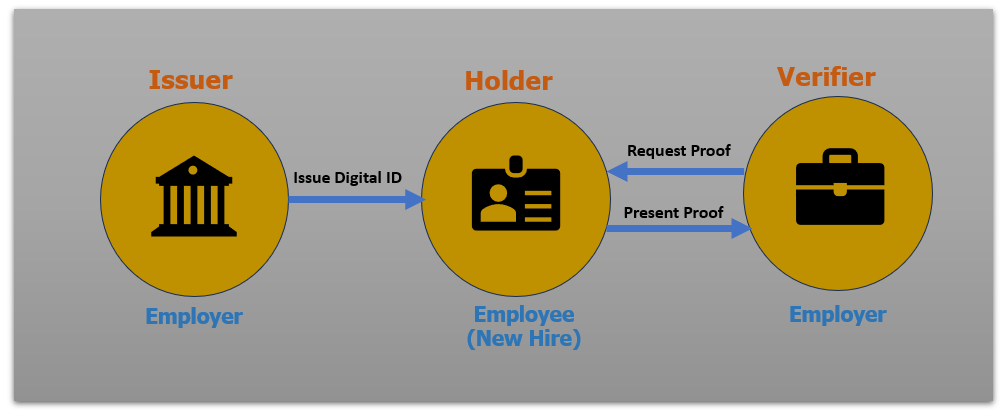
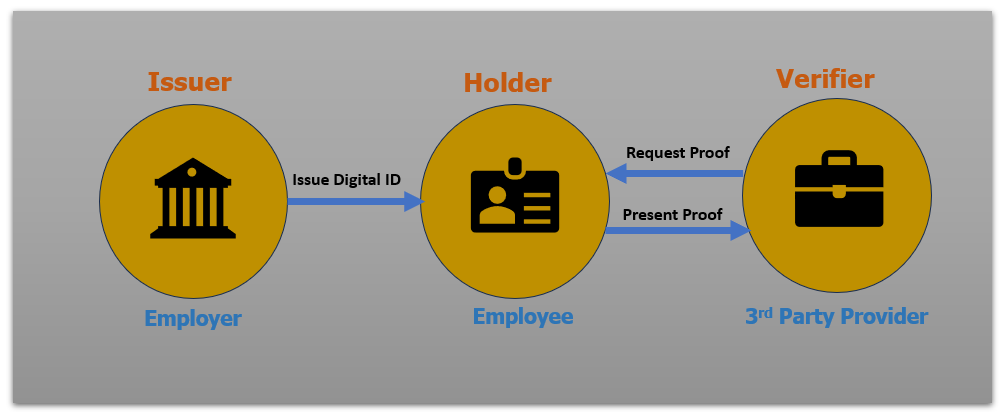
Chapter 3 : Microsoft Way
Microsoft Entra ID Verified ID is a system designed to confirm someone’s identity securely. Here’s a simple breakdown of how it works:
- Registration: First, you sign up for Entra ID Verified ID by providing some personal information, like your name, email, and possibly a photo ID.
- Verification Process: Microsoft then checks this information against trusted databases to make sure it’s valid. This might include verifying your ID document, checking against government records, or using other methods to confirm your identity.
- Confirmation: Once Microsoft confirms your identity, they give you a special digital ID. Think of it like a digital badge that proves you are who you say you are.
- Using Your ID: Now, whenever you need to prove your identity online, you can use your Verified ID. Websites or services that support this system can ask you to prove your identity, and you can provide your verified ID to confirm it securely.
- Security Measures: Verified ID uses encryption and other security measures to protect your information. This helps prevent identity theft and keeps your data safe.
Microsoft is collaborating with a varied community to develop a Decentralized Identity solution, empowering individuals to manage their digital identities autonomously. This solution ensures security and privacy by allowing users to oversee identity data without dependence on centralized authorities or intermediaries.
Decentralized Identity (DID)
Users constantly grant apps and devices access to their data, making it difficult to keep track of who has access to what information. Enterprises also face challenges in securely exchanging data with consumers and partners while maintaining privacy and security.
DID utilizes the Blockchain Technology also used by Bitcoin and other cryptocurrencies to create a digital identity where the user has control over their own identity data like in Cryptocurrency you have the control over your Digital Currencies not the Bank.
Microsoft collaborating with below open standards-based Decentralized Identity system that can revolutionize user experiences, offering greater control over data for both individuals and organizations.
- W3C Decentralized Identifiers
- W3C Verifiable Credentials
- DIF Sidetree
- DIF Well Known DID Configuration
- DIF DID-SIOP
- DIF Presentation Exchange
These system promises enhanced trust and security for apps, devices, and service providers.
Verified Credentials
Verifiable credentials are data entities containing assertions made by the issuer, affirming details about a subject. These assertions are structured by schema and encompass the DID of both the issuer and the subject. The issuer’s DID generates a digital signature, serving as evidence of their affirmation of the provided information.
How everything works in conjunction
The below Diagram (Courtesy: Microsoft) shows how it works
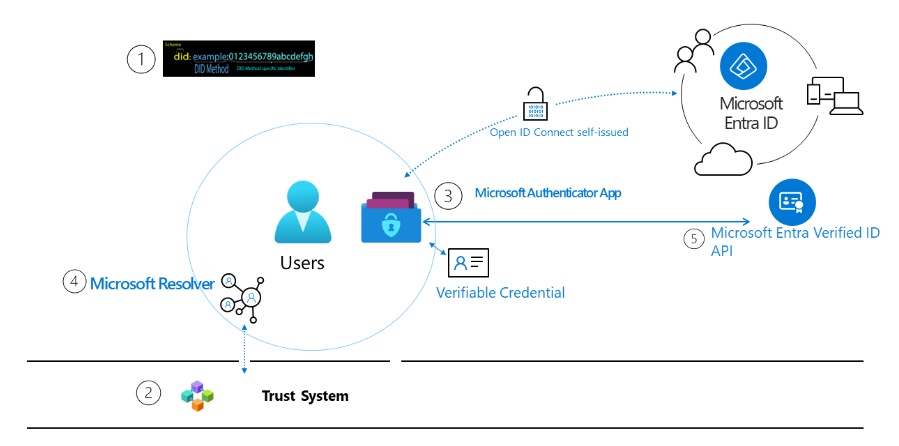
- W3C Decentralized Identifiers (DIDs): Users create, own, and control unique IDs independent of organizations or governments. Linked to Decentralized Public Key Infrastructure (DPKI) metadata, comprising JSON documents with public key material, authentication descriptors, and service endpoints.
- Trust System: DIDs are typically recorded on networks representing trust systems for resolving DID documents. Microsoft supports DID:Web, a permission-based model utilizing a web domain’s reputation.
- DID User Agent/Wallet: Microsoft Authenticator App allows real people to use decentralized identities and Verifiable Credentials. It creates DIDs, facilitates issuance and presentation requests, and manages DID seed backup through an encrypted wallet file.
- Microsoft Resolver: API for looking up and resolving DIDs using the did:web method, returning the DID Document Object (DDO) containing associated DPKI metadata such as public keys and service endpoints.
- Microsoft Entra Verified ID Service: Azure-based issuance and verification service with a REST API for W3C Verifiable Credentials signed with the did:web method. Enables users to generate, present, and verify claims, fostering trust between system users.
In next blog post, we will demonstrate how to configure Entra ID Verified ID using a real life example.
♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥Thank You for Reading, See you in the next Blog♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥
Many thanks for this article. I would also like to convey that it can become hard when you find yourself in school and just starting out to create a long credit ranking. There are many individuals who are just simply trying to make it and have a protracted or favourable credit history can often be a difficult factor to have.