In order to understand Microsoft Defender Products and Family, we need to take a step back and first need to understand Microsoft Infrastructure and OS coverage.
Home/On-Premise
Windows OS running on Private/Home Devices.
Windows OS running on Corporate/Office Devices.
Cloud/Microsoft Datacenter
Microsoft 365 provides SaaS (Software as a Service) based solutions like Microsoft 365, Intune, PowerBI etc.
On the other hand, Microsoft Azure provides IaaS (Infrastructure as a Service) and PaaS (Platform as a Service) solutions like Virtual Machines, Networks, Databases, Storage, App Service, IoT etc.
Microsoft Defender is a Security Solution which provides protection for all the above-mentioned Infrastructures and OS which we will discuss in this Blog.
In Part -1 we will discuss about Microsoft 365 Defender
In Part -2 we will discuss about Microsoft Defender for Cloud
In Part -3 we will discuss about Microsoft Defender for IoT
In Part -4 we will discuss about Microsoft Defender for Standalone OS
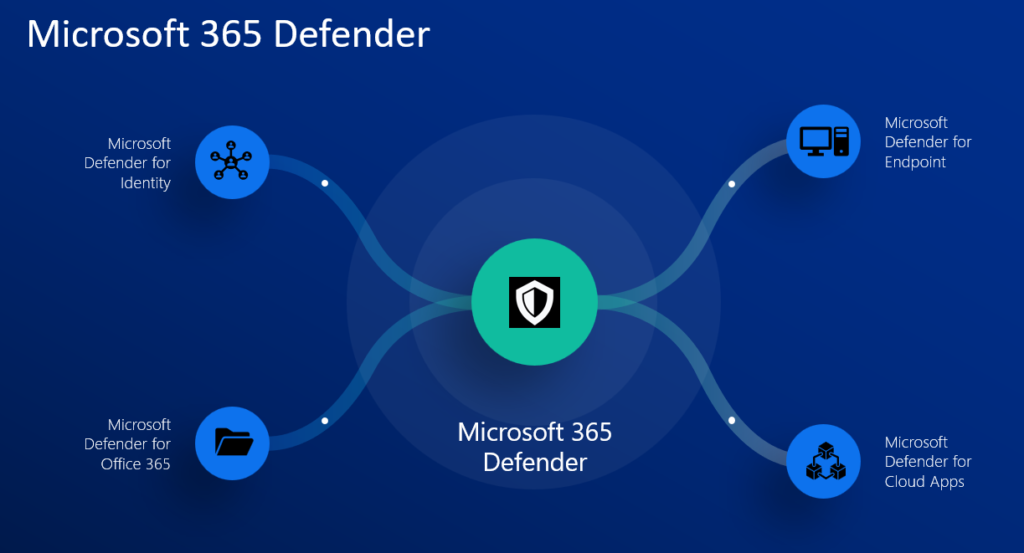
Microsoft 365 Defender
Microsoft 365 Defender is an integrated pre and post-breach enterprise security suite that orchestrates detection, prevention, investigation, and response across endpoints, identities, emails, and applications to provide unified protection against advanced attacks.
Microsoft 365 Defender products and solutions
Microsoft Defender for Endpoint provides best-in-class endpoint protection for Windows, macOS, Linux, Android, iOS, and network devices, enabling businesses to quickly stop attacks, extend security resources, and evolve defenses. Have confidence in your security approach because Microsoft Defender for Endpoint gives you the tools and insights you need to gain a holistic view of your environment, mitigate advanced threats, and respond immediately to alerts in one unified platform.
License Requirements –

Capabilities –
- Asset discovery
- Discovery of endpoints and network devices connected to your corporate network.
- Onboard discovered devices and secure them using integrated workflows.
- Review assessments and address threats and vulnerabilities on newly discovered devices.
- Threat & Vulnerability Management (TVM)
- Detect risk across managed and unmanaged endpoints with built-in-modules and agentless scanners, even when devices aren’t connected to the corporate network.
- Eliminate periodic scans and access entity-level inventories of devices, software, digital certificates, and browser extensions.
- Continuously assess endpoints and customize profiles against Microsoft benchmarks and industry standards, including CIS and STIG.
- Use Microsoft threat intelligence, breach likelihood analysis, business contexts, and endpoint assessments to understand and prioritize vulnerabilities.
- Focus on threats that pose the highest risk with a single view of prioritized recommendations from multiple security feeds.
- Proactively block known vulnerable versions of apps or warn users with customized desktop alerts.
- Connect teams with built-in workflows and integrations. Track progress and trends in real time with remediation tracking and device reports.
- Attack Surface Reduction (ASR)
- Provides Application Guard and Application Control.
- Reducing your attack surface with ASR rules.
- Provides controlled folder access.
- Device Control protection for unauthorized removable storage media.
- Network protection to prevent Users from using any application to access dangerous domains that may host phishing scams, exploits, and other malicious content on the internet.
- Web threat protection, Web content filtering, and Custom indicators.
- Exploit protection helps protect against malware that uses exploits to infect devices and spread.
- Manage Defender Firewall with advanced security.
- Next-Generation Protection (NGP)
- Metadata-based ML engine – Specialized ML models, including file type-specific models, feature-specific models, and adversary-enhanced monotonic models, analyze the highlighted descriptions of suspicious files sent by customers.
- Behavior-based ML engine – Real-time cloud ML models are used to analyze the behavior of the process tree in response to suspicious behavior sequences and sophisticated attack methods that are monitored on the client. Attack methods that are being watched include lateral movement, exfiltration, and all stages of the attack chain, including exploits, elevation, and persistence.
- AMSI-paired ML engine – To identify sophisticated threats like fileless and in-memory attacks, pairs of client-side and cloud-side models conduct advanced analysis of scripting behavior prior to and after execution. There are two models for each of the scripting languages covered by these models, including PowerShell, JavaScript, VBScript, and Office VBA macros.
- File classification ML engine – An additional layer of protection against attacks that call for additional investigation is provided by multi-class, deep neural network classifiers that look at the entire contents of files. Files that are deemed suspicious are prevented from running and categorized by the cloud security service. Full-content deep learning models can classify a file in a matter of seconds and respond to the client by allowing or blocking it.
- Detonation-based ML engine – In a sandbox, suspicious files are destroyed. To prevent attacks, deep learning classifiers examine the observed behaviors.
- Reputation ML engine – For the purpose of blocking threats connected to malicious or dubious URLs, domains, emails, and files, Microsoft’s domain-expert reputation sources and models are queried. The Microsoft Intelligent Security Graph uses sources such as Windows Defender SmartScreen for URL reputation models and Office 365 ATP for email attachment expert knowledge.
- Smart rules engine – Based on researcher expertise and a community’s understanding of threats, smart rules written by experts identify threats.
- Endpoint Detection & Response (EDR)
- Give your security operations center access to in-depth knowledge, cutting-edge threat monitoring, and analysis. Detect attacks and zero-day exploits using sophisticated behavioral analytics and machine learning.
- Automation investigation and remediation (AIR)
- Investigate alerts automatically, then take immediate action to eliminate complex threats. Apply best practices and intelligent decision-making algorithms to spot live threats and decide what to do about them.
- Microsoft Threat Experts
- Endpoint Attack Notifications is a managed threat hunting service that was formerly known as Microsoft Threat Experts. Following application and acceptance, Microsoft threat experts will send you endpoint attack notifications so you won’t miss any serious threats to your environment. You can use these notifications to safeguard the endpoints, email, and identities of your company.
Microsoft Defender for Office 365 protects your business from harmful threats brought on by emails, links (URLs), and collaboration tools like SharePoint, Teams, Yammer, etc.
License Requirements –

Capabilities –
- Built on Microsoft’s 24 trillion daily security signals.
- Low latency file detonation—average <45s.
- Enhanced spoof protection beyond DMARC (Domain-based Message Authentication, Reporting, and Conformance) checks.
- Internal email protection within compliance boundary.
- Easy identification of configuration flaws, vulnerable users.
- Powerful phishing simulation using direct injection.
- No whitelisting required of IP’s and URLS.
- Detailed reporting of clicks, IPs, devices and browsers used.
- Advanced protection for Teams, SharePoint, and OneDrive.
- Time-of-click protection within Office 365 apps (Word, Excel, PowerPoint) and Microsoft Teams.
- Native hover experience to show original URLs for wrapped links.
- Priority Account Protection tracks critical users.
- Enriched details for SOC effectiveness.
- Ability for SecOps to submit emails, URLs, files to Microsoft for analysis.
- Configurable sending limits to limit scope of breach.
- XDR integration to amplify prevention, detection, and response across Microsoft products.
- Automated Investigation and response integration across Defender for Office 365, Defender for Endpoint, Defender for Identity, Defender for Cloud Apps, and Azure Active Directory.
- Powerful advanced hunting across the digital estate.
Microsoft Defender for Identity is a cloud-based security solution that makes use of your on-premises Active Directory signals to recognize, detect, and investigate advanced threats, compromised identities, and malicious insider actions targeted at your company.
License Requirements –

Capabilities –
- Proactively identify security posture assessments to help SecOps to find and remediate on premises Identity vulnerabilities. For e.g
- Entities exposing credentials in clear text
- Legacy protocols usage
- Weak cipher usage
- Unsecured Kerberos Delegation
- Domain Controllers with Print Spooler service available.
- Exposure of inactive/expired accounts in sensitive groups
- Unmonitored domain controllers
- Microsoft LAPS usage
- Risky Lateral movement paths
- Unsecured SID history attributes
- Unsecured account attributes
- Inspect Network traffic related to NTLM, Kerberos, LDAP, RPC, DNS and SMB.
- Profile Users and entities behavior, identify behavior anomalies.
- Data enrichment and correlation in the cloud for real time detection.
- Extending support to ADFS servers for advanced Identity protection.
- Prioritization of threats and identity-based attack investigations.
- Automated threat detection and incident response.
Microsoft Defender for Cloud Apps is a Cloud Access Security Broker (CASB) that supports a number of deployment methods, including log collection, API connectors, and reverse proxy. To detect and counteract cyberthreats across all of your Microsoft and third-party cloud services, it offers comprehensive visibility, control over data travel, and sophisticated analytics.
License Requirements –

Capabilities –
- Discover and control the Risk of Shadow IT
- Discovery of Shadow IT across SaaS, IaaS and PaaS.
- Understand the risk of your SaaS apps
- Analyze usage patterns
- Block risky and unsanctioned apps
- Continuous monitoring
- Protect your files and data in the cloud
- Detect and remediate overexposed files and anomalies
- Classify and protect your data no matter where it’s stored
- Monitor, investigate and remediate violations
- Protect against cyberthreats and anomalies
- Detecting and protecting against cloud-native threats, like Insider threats, Malware, Ransomware, Rogue Application, Data exfiltration and Compromised Accounts.
- All the Detections are powered by Microsoft Threat Intelligence.
- OAuth App Permissions.
- Assess the compliance of your cloud apps
- Check to see if your cloud apps adhere to all applicable compliance requirements, such as legal compliance and industry standards. Limit access to regulated data and stop data from leaking to apps that are not compliant.
♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥Thank You for Reading, See you in the next Blog♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥