Microsoft Defender for Cloud
- Protects the workloads running in Azure, On Premise as well as other Cloud Platforms like AWS and GCP.
- Strengthens the Security posture of Multi Cloud platforms like Azure, AWS and GCP.

- Defender for Cloud assesses your Multi Cloud and On-Premise environment resources compared with the guidance in MCSB (Microsoft cloud security benchmark) and generates a Secure Score.
- Depending upon the secure score it provides the hardening guidance to efficiently and effectively improve your security score.
- Gives you a visibility of your Current security situation and depending upon your Company’s Compliance requirement you can customize the standards used to assess your compliance, and add other regulations (such as NIST and Azure CIS) or organization-specific security requirements (such as GDPR, PCI-DSS).
- Builds a cloud asset inventory, connections and lateral movement possibilities between resources, exposure to internet, permissions, network connections, vulnerabilities and more.
- Repetitive scans throughout the cloud environment expose the attack paths and suggest recommendations on how to break the attack paths and prevent successful breach.
- Provides security alerts powered by Microsoft Threat Intelligence for large range of APT (Advanced Persistent Threat) attacks.
- Protects all your resources like Azure Native, On-Premises and other Clouds (such as AWS and GCP) under one roof.
- Defender for Cloud offers defenses against different workloads (such as Compute, Data and Service layers) which we will discuss in details.
From the Defender for Cloud Portal->Settings you can enable individual workloads plan or enable for all and depending upon the enablement pricing for each workload will be calculated.
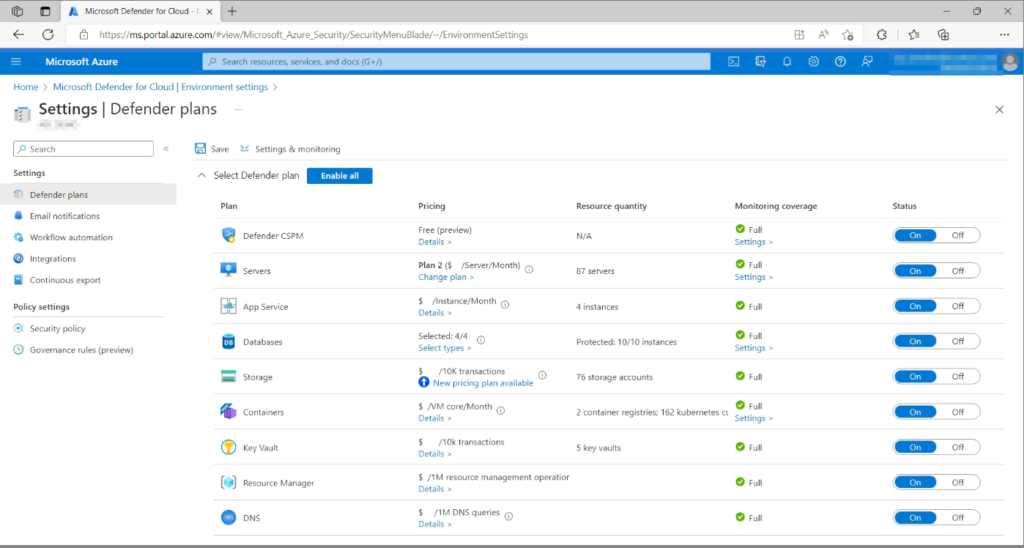
Pricing Requirement-
As we have seen in the Part 1 blog, that Defender for 365 is primarily responsible for User Identities, Devices and Apps hence it was based on Licenses whereas Defender for Cloud is responsible for Server-side components like Servers, Storage, Databases etc and hence it uses Pricing scheme based on Workloads. Below are the Pricing for Defender for Cloud components for Region Central US and in US Dollars.
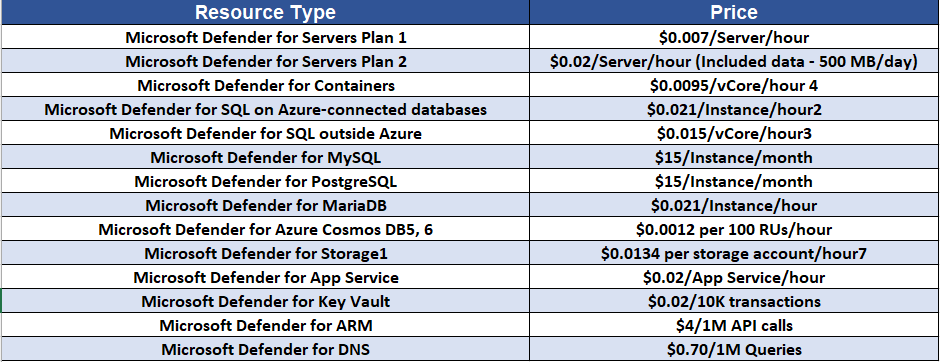
Note – Defender for Cloud is Free for First 30 Days. Any usage beyond 30 days will be automatically charged as per the pricing model.
Microsoft Defender for Cloud Products and Capabilities.
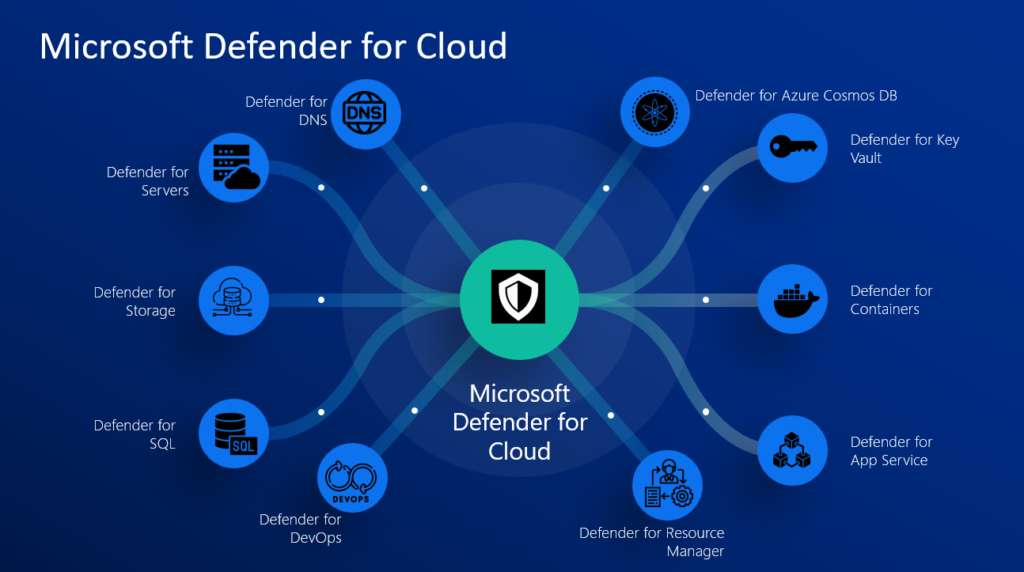
Microsoft Defender for Servers protects your Windows and Linux devices across Azure and other Clouds (such as AWS or GCP).
Capabilities –
Defender for Servers Plan 1
- Provides Unified view under Defender for Cloud portal to display Defender for Endpoint alerts to drill down.
- Automatic MDE provisioning to Azure, AWS and GCP workloads.
- Real time Vulnerability Management without other agents or periodic scans.
- Detects threats at OS level including VM behavioral and Fileless attack detections.
Defender for Servers Plan 2 (Includes Plan 1 features + the below ones)
- Detects threats at the Network level for Azure virtual machines.
- In addition, Vulnerability Management provides deeper analysis on risks related to browser extensions, network shares and digital certificates.
- Provide customized Security Policy and Regulatory Compliance as per Industry standards and benchmarks.
- Log Analytics 500 MB free data ingestion from Servers and VM using Log Analytics agent.
- Adaptive application controls to allow lists of Safe applications for devices.
- File Integrity Monitoring (FIM) examines the changes in files and registries to detect any threats.
- Provides Just-in-time VM access for locking down Management ports to reduce attack surface.
- Adaptive network hardening to filter to and fro network traffics.
- Access Docker containers and compare them with the Center for Internet Security (CIS) Docker Benchmark.
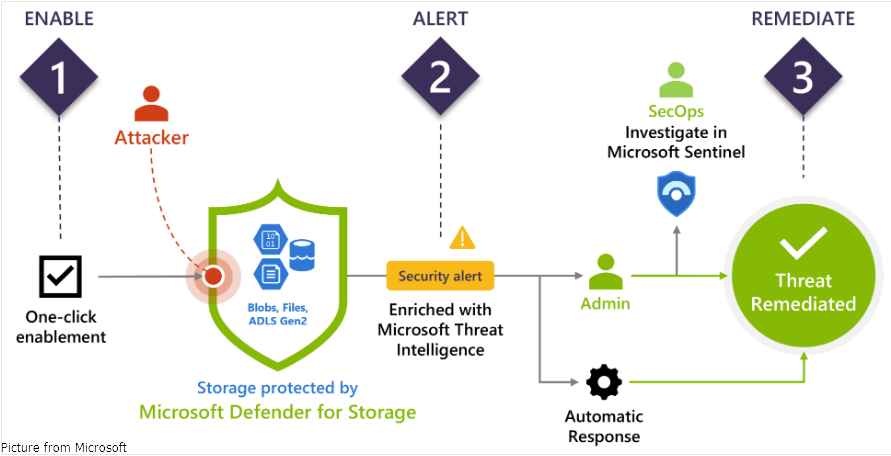
Microsoft Defender for Storage is a Azure native Storage security solution that looks for suspicious and potentially dangerous attempts to access or exploit your Azure storage accounts. For the purpose of providing contextual security alerts, it makes use of Microsoft Threat Intelligence data and advanced threat detection capabilities. These alerts also contain instructions on how to mitigate any threats already identified and stop attacks in the future.
Capabilities –
- Centralized security solution for Azure Blob, Azure Files and Data lakes services to investigate and recommendation to remediate potential Threats.
- Can trigger alerts based on following threats
- Unusual access to an account.
- Unusual behavior in an account.
- Hash reputation-based Malware detection.
- Unusual file uploads.
- Public visibility.
- Phishing campaigns.
- Powered by Microsoft Threat Intelligence it can detect highly sophisticated attacks to Storage accounts like unauthenticated access, compromised credentials, social engineering attacks, data exfiltration, privilege abuse, and malicious content.
- With Azure Cloud Automation using Logic Apps it can prevent and respond to identified threats as shown below.
Microsoft Defender for SQL extends to protect Azure, On Premise as well as AWS and GCP SQL workloads. It helps to detect and mitigate possible vulnerabilities and malicious activities across all SQL workloads.
Capabilities –
- One stop security solution for all SQL Workloads (such as Azure SQL DB, SQL Managed Instances and Dedicated SQL pool in Azure Synapse) residing in Multi Cloud as well as on Premise environment.
- Does Vulnerability Management to discover, track and remediate SQL vulnerabilities.
- Provides advanced threat protection such as SQL Injection attacks, Suspicious DB access or activities and Privilege abuse.
Microsoft Defender for Containers is a security solution to improve and maintain security of your Kubernetes clusters, containers and their applications across Multi Cloud (Azure, AWS and GCP) as well as Kubernetes On-Premises.
Capabilities –
- Continuous assessment of Kubernetes Clusters to find misconfigurations and provides necessary recommendations to fix it.
- Scans the containers in Azure Container Registry (ACR) and Amazon AWS Elastic Container Registry (ECR) to find and provides required guidance to remediate the Vulnerabilities.
- Provides real-time threat protection for your containerized environments and generates alerts for suspicious activities.
Microsoft Defender for App Service is a security solution to Identify and provide recommendations to mitigate the Threats against your Web Apps and API’s running on Azure App Services platform.
Capabilities –
- It utilizes other Azure Services to detect the attack vectors used by an Attackers to probe and exploit weaknesses in an App Service.
- Provides detailed recommendation to harden your App Services.
- Powered by Microsoft Threat Intelligence it can trigger alerts if the Web App is accessed from malicious IP Addresses.
- It can detect if an attacker runs Vulnerability scans against your App Service, privilege or Linux commands, fileless attack behavior, digital currency mining tools, and many other suspicious and malicious code execution activities.
- It can also detect DNS Dangling attacks (DNS Dangling is when you decommission an Internet facing Web App however you forget to delete its record from DNS Registrar. An attacker may take over that subdomain and use it for malicious activities).
Microsoft Defender for Key Vault provides an additional layer of threat protection and intelligence for Azure Key Vault which safeguards encryption keys, secrets, Certificates and Passwords.
Capabilities –
- It alerts and sends email when it detects any unusual activities and potentially harmful attempts to access or exploit Key Vaults.
- Provides additional information on how to investigate and remediate threats.
- If a threat to Key Vault originates from an unknown source it provides necessary steps to respond and if the source is known it helps you to contact the User or Application Owner.
Microsoft Defender for DNS provides an extra layer of protection for the Applications that use Azure DNS Service without the need of any additional agents.
Capabilities –
- It can detect suspicious and malicious activities like:
- Data exfiltration from your Azure resources using DNS tunneling.
- Malware communicating with command-and-control servers.
- DNS attacks – communication with malicious DNS resolvers.
- Communication with domains used for malicious activities such as phishing and crypto mining.
Microsoft Defender for DevOps gives security teams the ability to safeguard resources and applications from code to the cloud in multi-pipeline environments like GitHub and Azure DevOps through the use of a central console.
Capabilities –
- Provides a unified visibility into the DevOps inventory and the security posture of the application code used for pre-production, including the results of vulnerability scans for code, secret dependencies, and open-source dependencies for mutli-cloud and multi-pipeline environment.
- Strengthen the resource misconfigurations throughout the development lifecycle before reaching out to Production environment.
- Utilize Defender for Cloud’s comprehensive code to contextualize cloud insights. Security administrators can assist developers by assigning developer ownership and helping them prioritize critical code fixes with Pull Request annotations.
Microsoft Defender for Azure Cosmos DB powered by Microsoft Threat Intelligence can detect SQL Injections attacks, suspicious access patterns and exploits caused by compromised identities or malicious actors.
Capabilities –
- It provides security alerts for any malicious activities and necessary recommendations to mitigate the threats.
- The alerts comprise of SQL Injection attacks made to Cosmos DB, suspicious access patterns from unknown IP or location and suspicious activities caused by threat actors.
Microsoft Defender for Resource Manager keeps track of all the resource management activities performed via Azure Portal, Azure REST API’s, Azure CLI or other Azure Programmatic clients. With cutting edge security solution it can detect advanced threats and alerts you about any malicious activities.
Capabilities –
- It protects against suspicious RM operations from malicious IP addresses, disabling antimalware and suspicious scripts running in VM extensions.
- Blocks the usage of exploitation toolkits like Microburst or Powerzure and lateral movement from Azure management layer to Azure resources data plane.
♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥Thank You for Reading, See you in the next Blog♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥♥